HID DigitalPersona
The HID DigitalPersona software (formerly Crossmatch) offers a new way to provide authentication services to users. Whereas traditional 2FA/MFA solutions are stuck on “what you have/what you know”, DigitalPersona leverages an array of easily deployable authentication methods so users can quickly and easily gain access to their network resources. Balancing security and usability, this solution employs one of the widest arrays of authentication factors in the industry. This includes one-time passwords, mobile-based push, smartcards, USB keys, risk- and context-based methods, and biometrics, such as fingerprint, face, and behavioral keystroke.
- Deploys on Windows Active Directory or LDS server
- Has a user-friendly interface for easy self-enrollment of credentials and authentication policy enforcement
- Provides a browser-based SSO Portal for accessing SAML-enabled apps
- Offers an optional Password Manager feature to securely store, update and auto-fill passwords
- Is available in a variety of Configurations: SSO, Windows Logon, Premium Edition, and as part of the HID ActivOne Subscription
Overview
HID’s DigitalPersona® transforms the way IT executives protect the integrity of the digital organization by going beyond traditional two-factor and multi-factor authentication. DigitalPersona Premium builds on the fast and secure Windows® Logon and VPN access found in DigitalPersona Logon for Windows, adding advanced integration options to secure all applications, systems and networks. Additional client and server components included in Premium are SSO (SAML), Access Management API and Password Manager modules. Premium offers the ability to deploy the optimal set of authentication factors for every user, application, device and network — moment by moment. It accomplishes this while uniquely serving IT through unparalleled ease of integration and ongoing maintenance.
Step 1: Evaluate Requirements
We begin with a 30-60 minute call to go over the end users requirements. We listen to the use cases, and make a recommendation of what solutions will work best in the environment.
Step 2: Quote
Once we determine the appropriate solution, we can then make a recommendation for the client and provide a preliminary pricing proposal.
Step 3: Demo
If the pricing aligns with the end client's budget, we offer a free demo of the selected solution which typically takes around 60 minutes. This is a great time for clients to ask detailed questions about the proposed solutions.
Step 4: Pilot
After the demo is completed, we offer to set up a free 30 day pilot (remotely) on the end users network. This gives the customer a chance to experience the solution in a real world enviornment.
Step 5: Installation
If the client's testing is successful and a purchase order has been submitted, the Tx Systems engineering team will assist in turning the pilot test into a full production install. This portion may require the client to purchase a professional service package.
Step 6: Ongoing Support
Ongoing maintenance and support is covered by each solution's active maintenance agreements. As long as the client reinstates their maintenance every year, then they will receive support via both Tx Systems and HID engineers for the life of the system.
Integration Options
SSO (SAML)
- Integration of SAML enabled applications
- SSO application portal on both Window and mobile platforms
- Customers options to remove all passwords
Access Management API
- Comprehensive DigitalPersona API management enables tightly integrated implementation
- Full scalability across on-premise and cloud services
Password Manager
- Secure and convenient authentication application overlay
- Allows customers to quickly provision apps without modifying source code
Windows Logon
- Out of the box integration with Windows logon
- Includes all factors including contextual and risk-cased
- Up to 3-FA, any combination
What Our Customers Are Saying
You have no idea how long we have been wanting to get this done. So glad it is finished. These guys are great to work with.
Bank/Credit Union | CTO | 300 users
Nobody in our IT department has had much experience with MFA so it is not our area of expertise. Tx Systems was very helpful and DigitalPersona has been easy to use.
Fortune 500 Company | IT Admin. | 4000 users
We've been putting off implementing multi-factor authentication for months. The team at Tx Systems were experts and helped us satisfy all of our federal mandates.
DoD Federal Contractor | Owner | 500 users

99.9% of account hacks could be blocked with MFA, according to Microsoft (August 2019)
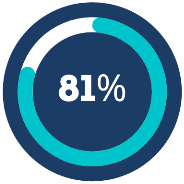
81% of breaches are caused by passwords that were either weak and/or stolen passwords (August 2018)
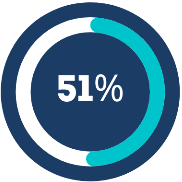
51% of data breaches include some type of malware to steal login credentials (August 2018)
In the OWASP Top 10 application security risks, "Broken Authentication" is ranked #2