

Background
TAA Compliance is necessary for products bought and used by the US government, but it teaches us all a crucial lesson about security. Essentially, the Trade Agreements Act (TAA) states that certain products must be made in the USA or an approved country. This act was originally passed in 1979 to promote fair trade in the global market, but now it serves another purpose: keeping vital information out of the wrong hands.
How to Meet TAA Compliance
GSA contracts require TAA compliance, which is met one of two ways:
- The item is entirely (100%) produced, grown, or manufactured in the United States or a designated nation. Approved designated countries include Taiwan, Canada, Mexico, Australia, Japan, Germany, and many others. A full list of TAA compliant countries can be found here.
- The item is “substantially transformed” (>50%) into a new and unique article of commerce within the United States or designated country. The item now has a name, character, or usage that differs from its original production.
Non-Compliant TAA Countries
It's crucial to remember that not every nation complies with TAA. Notable non-TAA compliant nations include Malaysia, Vietnam, China, India, and Russia. These nations' products and services are not eligible for TAA compliance and are not permitted to be utilized in federal contracts. The federal government avoids products made by these countries, especially in the security sector, due to the potential for foreign interference. It is a good idea for every business that prioritizes security not to compromise on the origin of their products.
When it comes to your security infrastructure, it is crucial you know what you have, how it works, and where it came from. Buying from companies that have anti-American interests in mind may pose devastating security risks– especially when matters of national security come into play.
Spotlight: Examining Chinese Hardware & Software
A recent example of foreign security devices posing unsuspecting, yet potentially severe, threats has been detailed by KrebsOnSecurity. They had gotten a report from a reader codenamed “Mark” for anonymity. Mark was issued a government smart card intended for civilian personnel called a Personal Identity Verification (PIV) card. These cards are used for granting access to federal facilities and information systems. Active duty uniformed personnel, DoD civilian employees, and selected reserve use Common Access Cards (CAC) which function similarly. Many employees are granted access to federal information systems which include security, filing, and payroll systems, databases, and programs spanning across every branch of government entities.
Since 2020’s stay-at-home order and the continued trend of people working from home, many users access office systems remotely. Access to government systems, whether remote or in office, relies on a secure logon which frequently couples the employees CAC or PIV card with a smart card reader and middleware. Oftentimes, however, the government will not issue smart card readers for out of office use, leading to many users buying potentially suspect products. Mark was one of those people. He had bought a $15 smart card reader from Amazon that was advertised as meant to handle US government CAC/PIV cards. The reader sold by Saicoo was the first option when “PIV card reader” was searched and had a fair amount of mostly positive reviews.
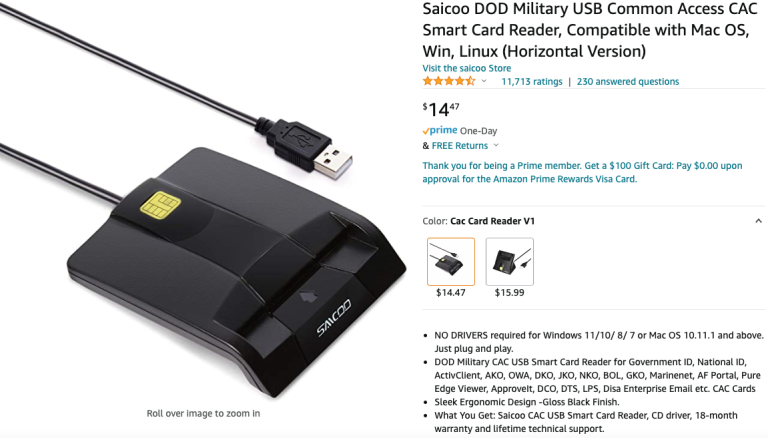
When the reader arrived, Mark plugged it in but received error messages about the devices hardware drivers incorrectly functioning. Windows recommends he check the company's website for updated drivers. Downloading drivers can be extremely risky if you aren't entirely sure it is coming from a reputable source. Mark knew this and cautiously submitted Saicoo’s driver files to Virustotal.com. This website scans shared files with over 5 dozen security products. It reported 43 security tools detecting malicious coding in the driver and identified it harbored a malware known as Ramnit. This malware is a nasty trojan horse that spreads by attaching itself to files on your computer.
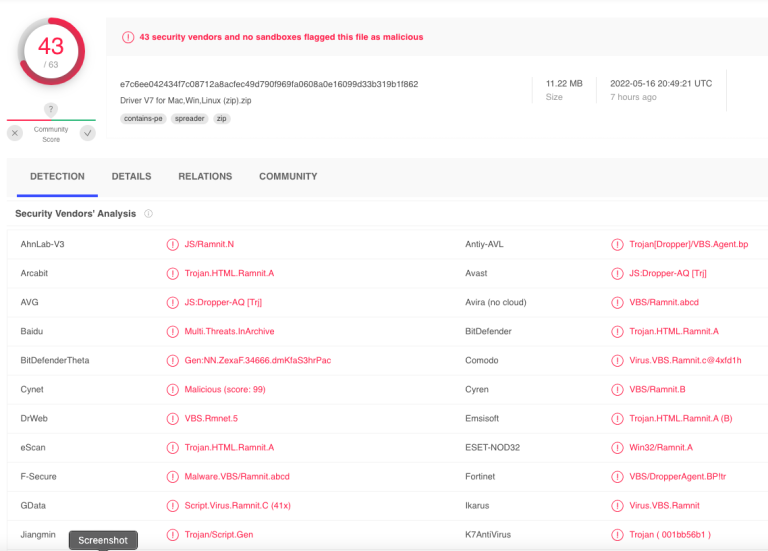
“Seems like a potentially significant national security risk, considering that many end users might have elevated clearance levels who are using PIV cards for secure access,” Mark said.
Know Who You Buy From
An alarming amount of vendors claim TAA compliance when they list security products; HOWEVER THEY ARE NOT COMPLIANT as they are Chinese/Non-American companies. Beware especially when buying from Amazon– reviews and star ratings are not what they seem. Along with the Saicoo example, our experts have compiled a list of Non-TAA compliant companies, see below:
Saicoo Senone Rocketek
Takya URFACE Mtakyi
Fongwah Luckeswn Zoweetek
Buying security products directly from reputable US companies is the safest way to ensure your data isn't in the hands of foreign actors with malicious intentions. Tx Systems Inc has been providing security solutions for the past 25 years– ensuring safety, security, and peace of mind for businesses big, and small, all over the world. Data security should always be in your hands. We put you in control by offering and implementing only the best security solutions from leading global manufacturers like HID, Identiv/Hirsch, Thursby Software Systems, SecuGen and more.
At Tx Systems, we understand that every business is unique, with its own set of challenges and requirements. That's why we take a personalized approach, working closely with our clients to assess their specific needs and develop tailored solutions that address their unique cybersecurity concerns. From identity and access management to threat detection and response, we have the tools and expertise to safeguard your organization's digital ecosystem. Our comprehensive range of identity and cybersecurity solutions is designed to help businesses mitigate risks, strengthen their security posture, and ensure compliance with industry regulations. Contact our team today to learn how we can help secure what matters most!



